Malware is the family name for some of the all-time most dangerous internet threats. Several types of malware are still widespread today. From the early 1960s, malware has evolved and diversified to perform all kinds of nefarious acts.
Attackers may use malware to steal your sensitive information (with a Trojan), access your accounts, or encrypt all your files (with Ransomware). But the list doesn’t end there.
Malware can cause countless malicious actions against whatever is connected to a network. From gathering your buying habits for selling that information to companies to provoking the destruction of physical components in a nuclear plant.
What is Malware?
Malware is the short form for Malicious Software. It includes any program having an evil intention like:
- Damaging,
- Disabling or limiting the control of a legitimate owner of a service, account, or tool,
- Taking control of a victim system.
Malware often has two main parts: a dropper and a payload.
The dropper delivers the payload on the target system by spreading and installing malicious codes. For example, a worm makes a copy of itself somewhere else when it has run. It typically breaks into other systems by using brute-forcing or code execution vulnerabilities.
Then, we have the payload, who takes the key role in the show. The payload code can do a diverse range of things.
In older times, the payload was typically used for gathering your information and giving remote access to your system. It is not rare nowadays, though. For example, in Operation Socialist, the UK Government Communication Headquarters (GCHQ) breached Belgian telecommunications company Belgamon. They installed malware to do surveillance of traffic passing through Belgium to other countries.
But the damage can also go to physical components in your system. That was the case with the Stuxnet worm, which targeted programmable logic controllers (PLCs) in Iranian nuclear plants to destroy fast-spinning centrifuges.
Last decade, malware payloads focused on using your hardware to mine cryptocurrency, taking your system as a “zombie” (Botnet) to perform other attacks, and on encrypting all your sensitive information to demand a ransom.
And a vast collection of payloads is publicly available, like here.
Malware Propagation Methods
There are different media that malware can use to get into your system. Some of the most common are:
- Free Software: For example, crack files. It usually contains malware belonging to the offering organization.
- File-Sharing Services: Torrent and P2P transfer data from many computers and either of these services could be infected.
- Removable Media: Like a USB, external hard disk, CD, or DVD. They can contain malware in the storage area or even in the firmware.
- Email: Malicious content can be included in the attachment or a URL in the body of the message.
- Browsing: When visiting a vile site, it may download malware to your computer automatically. You need security software to prevent it.
Symptoms of Malware
These are the most common signs you may experience when infected with malware:
- Strange files on your server,
- High resource usage. You may feel your system slower,
- Unexpected behaviors,
- Your server gets black-listed or blocked by security software in other services,
- Outgoing spam,
- Ingoing/outgoing unknown connections.
Types of Malware
We can classify malware by its way of operation and by its goals.
Virus
A virus is a self-replicating program. It can produce copies of itself by attaching with another program of any format. They can act when they are downloaded, may wait for the host to execute them, or stay in sleep mode for a predetermined time.
Worm
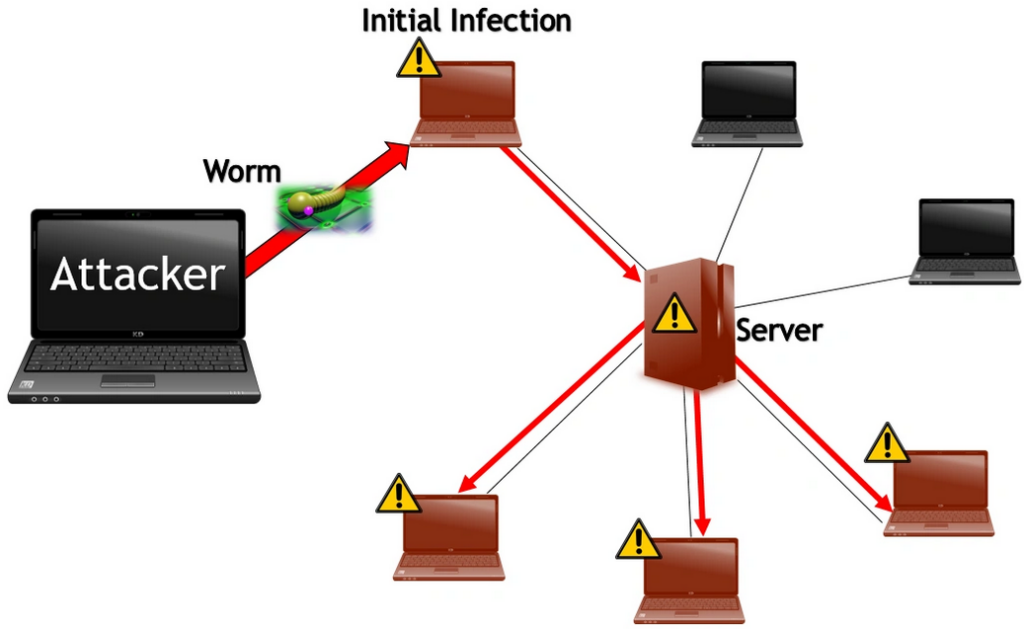
Unlike a virus requiring a triggering event to operate, worms can propagate by themselves. They can use different file transport protocols to infect other devices in a network. Samy Worm is an iconic case; it flooded the MySpace social network in 20 hours in 2005.
Spyware
Spyware gathers user interaction data such as email addresses, login credentials, keystrokes, GPS, voice recordings, etc. This information is sent to the attacker via a remote connection. Spyware hides its files and processes to avoid detection. The most common spyware are:
- Adware. It records your web surfing habits to bomb you with related ads and spam. For example, tracking cookies.
- Keylogger,
- And trojans.
The last one deserves a new section.
Trojan
A Trojan, referencing the old Greek history of the Trojan Horse, is a malicious program disguising as or inside another one. Trojans are typically spread by Social Engineering to create backdoors and monitor the host system. For example, the messaging app ANOM was a Trojan used by law enforcement to monitor criminals in a covert operation from 2018 to 2021.
Ransomware
Ransomware is the type of malware that made the most first-lines in the news last year. It even flourished a new illegal business: Ransomware as a Service (RaaS), offering ransomware kits in the Dark Web to as little as $100.
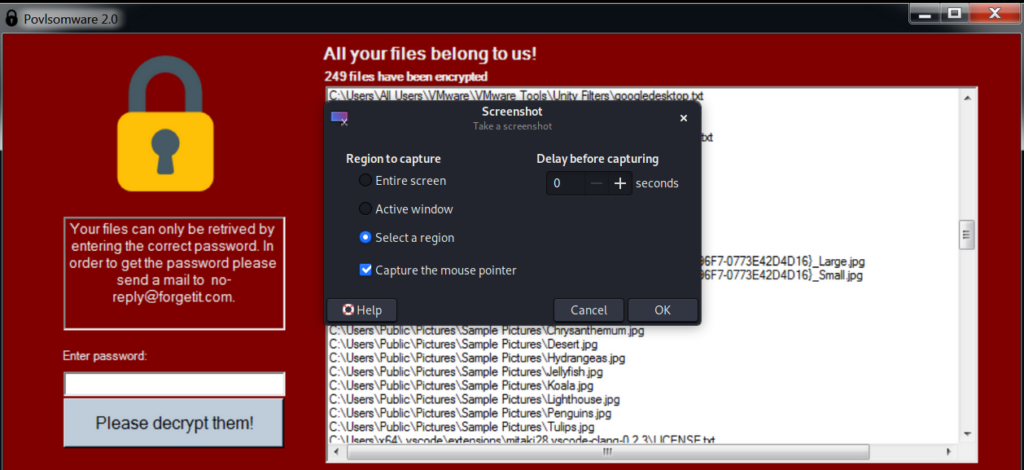
The major ransomware attack of 2021 (and one of the biggest all-times) victimized Kaseya, an IT solutions company. It affected Kaseya’s clients and their clients; more than one thousand companies all over the world.
Top Malware Statistics
WannaCry is considered one of the most harmful ransomware attacks in history. In 2017, this attack infected 7,000 computers in the first hour and 110,000 different IP addresses in the following two days.
Many companies in different countries lost control over their industrial processes, including car giants Renault and Honda.
According to the Mimecast 2021 State of Email Security Report, 61% of organizations experienced a ransomware attack that led to, at least, partial disruption of business operations. The previous year was 51%. We can see the attacks’ effectiveness on the rise.
How Can You Defend Against Malware?
Here’s a list of recommendations to better protect yourself.
Beware What You Click
Attackers often rely on users clicking on malicious links in emails, social media or pop-up ads that lead to malware installation.
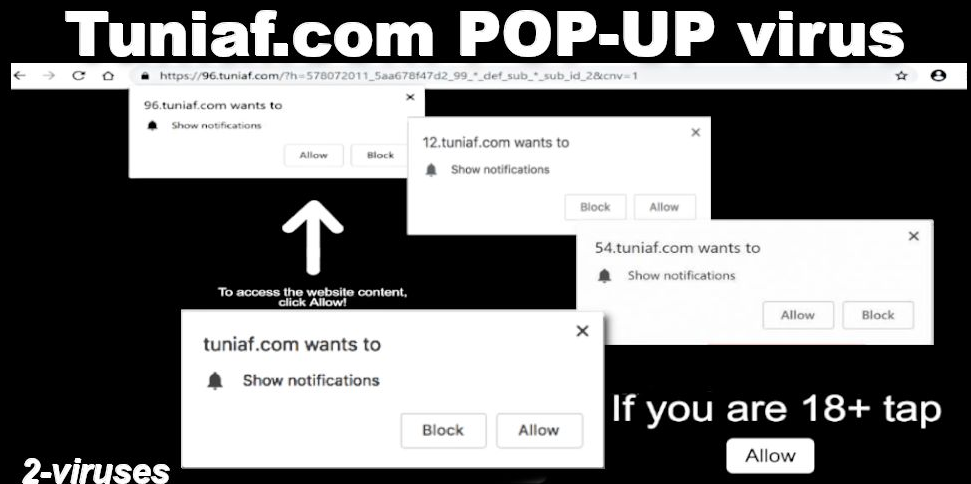
Even if you receive an email from someone you trust, the email still could have been sent by an attacker impersonating the person you trust.
Keep Your Systems and Software Updated
Malware sometimes relies on exploits for known vulnerable components to gain access or code execution in your server.
Browse Trustworthy Websites
Surf only renowned and secure websites using HTTPS. You will recognize when a website is using HTTPS by a closed lock icon next to your URL. If you are unsure you can trust a specific page, check here and in forums.
Download only Reputable Apps and Software
And do it only from trustworthy websites! A malicious app could contain malware. Remember what we mentioned before: free programs may come with surprises!
Use Security Software
An anti-virus, anti-spyware, ad blocker, a firewall, and an Intrusion Prevention System (IPS) are essential lines in your defenses. They monitor the behavior of your system and network in search of threats and act when necessary. For example, a firewall will block automatic downloads triggered by a malicious website when you are browsing.
An anti-malware software helps you to detect and remove, or in the best case prevent malware infections. Let’s analyze this in more detail in the following sections.
How can BitNinja Protect your Servers against Malware?
To be prepared for the unexpected, like a 0-day vulnerability, security should be applied in layers. You should protect each part of your system.
BitNinja has features specially designed to protect against malware:
- The Anti-Malware,
- The SandboxScanner,
- The Defense Robot,
- SiteProtection,
- And the Real-time IP Reputation system.
Why is BitNinja Different from other Anti-Malware Solutions?
BitNinja’s features are backed by state-of-art technology in different areas:
- The Anti-Malware module can detect malware in real-time even if its code is obfuscated because it uses a unique detection technique. One of our unique (SA-MD5) signatures equals thousands of traditional malware signatures.
- The Real-Time IP reputation module is constantly updated and vast list of malicious IPs worldwide. Attempts of connection coming from these IPs are blocked directly.
- Both of the above-mentioned modules are built on the Defense Network. Every BitNinja protected server worldwide shares information with each other about the most recent attacks. That’s how we can have 18 000 global blacklisted malware signatures and information about 100+ million IP addresses in our database.
- The SandboxScanner is a PHP emulator, which runs the PHP files on the server in a safe environment and automatically analyses the file’s behavior.
- The Defense Robot traces the backdoors used to infect your servers, to prevent future attacks. It correlates logs with malware catches and uploads attempts to determine the entry point and the intruder’s IP address.
- BitNinja SiteProtection helps you be up to date and secure by automatizing the patching of website vulnerabilities.
Example for Malware
Let’s analyze the 2021 Kaseya attack step by step.
First, the attackers got access to the Virtual System Administrator (VSA) and gained code execution exploiting zero-day vulnerabilities. At this point, the attackers turned Kaseya VSA software into a Trojan, which they used to install ransomware in Kaseya client’s systems.
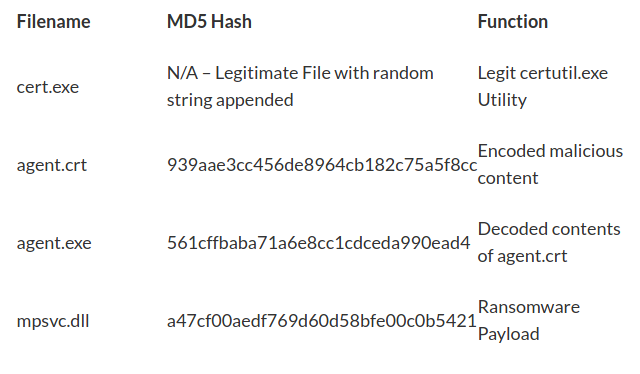
The malware contained an encryptor, which obfuscated the malicious content from the eyes of Kaseya and clients’ defense software. Finally, victims’ files were encrypted and taken as hostages demanding a ransom.
This example shows well how sophisticated and dangerous malware can get.
Credit: Source link